| Three Hundred |
| - Index Page |
| - About... |
| - By Year |
| Collections |
| - Comp-Grid |
| - Procedural |
| - Tactics |
| - Tiny Crawl |
| - Misc |
| Previous | Mechanic #026 | Next |
![[board1.png]](set02/img/entry025-board1.png)
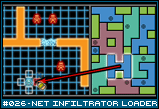
You may remember this image from the entry [#025 - Net Infiltrator Coder]. After you have successfully crafted a series of Tetris piece-like programs (or perhaps bought them from a store, or found them in a previous crawl), you have loaded them into your grid of memory located on the right side of the screen. You've left a few squares open in case you find new blocks of data during your travels and need to store them while you go. A block of data is 1 square high and between 1-3 squares wide. It can be rotated and placed in the grid for safe keeping. These blocks are then uncompressed back at home base to yield sensitive data that can be sold to the highest bidder or additional programs you could install in your system if you'd like. All prepared, you receive a job offer from a high profile plant food company. They want you to infiltrate the server farm of their biggest competitor and steal the recipe for their newest product. Your job is to break through their security, find the reciple, and steal it. You'll get additional reward for sabotaging their server, and of course, they'll buy any additional sensitive data you can find, like incriminating emails, security cam footage, trade secrets, and employee rosters. |
![[board2.png]](set02/img/entry026-board2.png)
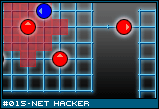
This is your mission. A server farm is a collection of nodes connected by data lines. Each shape represents a specific type of server, router, or switch. The circles, for example, are database servers. If you were looking for sensitive data, you'd probably want to check there first. The triangle is a security station, where various loggers, virus scanners, anti-intrusion devices, and what not come from. If you take down that server, the entire farm will have a slower response time and weakened security. The exact details of how the hacking process works aren't really worked out. I just wanted to give a frame of reference as to what exactly you are doing in this game. The ideas I have for how each of the servers and their connections are related will have to wait for some future entry, after I've had time to make the idea awesome.
|
![[load1.png]](set02/img/entry026-load1.png)
Alright, the hacker has arrived at a troublesome area. There is a red guard protecting a code gate, and past that gate are two more red guards. The hacker decides to load up an attacker program. To do this, he simply drags and drops one of the programs from the memory grid into his own install grid. After a short installation period, the new program spawns in the designated slot. No matter what shape the program is in memory, it is exactly 1x1 when installed. |
![[load2.png]](set02/img/entry026-load2.png)
The install grid is any touching square to the hacker or any of his installed programs. In this illustration, each of the red boxes is a loaded program. The hacker can install any new programs into any of the white framed squares. I should note that the installed programs should come with appropriate icons for their class, and colored according to their strength. Hopefully, the point is made without it. |
![[load3.png]](set02/img/entry026-load3.png)
Okay, here lies the rub. The installed programs are actually ATTACHED TO THE HACKER. That is, they have physical space in the game world, just like the player does. If the Hacker's avatar moves, the installed programs attached to it move as well. If the installed programs take up too much space, the player may not be able to fit through a doorway. If he stands too close to a wall, he may not have enough room to install further programs. Some programs may even bind you in place and you cannot move again until the program is released. |
![[load4.png]](set02/img/entry026-load4.png)
Luckily, the programs themselves are meant to be temporary. They do their business and then self quit. For example, the hacker approaches a code gate that he cannot get through. He installs a code-breaker program in front of him. After the program is installed, it will release an independent agent (fancy way of saying a unit you don't control). This agent will spawn from the program as if it were a docking station and then seek out any nearby code gates and attempt to crack it. After there are no more code gates, or at the player's request, it returns to the dock and de-installs itself. It can also be deleted if an enemy agent destroys either the agent or the docking station. Note that if you block in an agent's docking station while the agent is still in it, it cannot escape. Not all programs are agents though. Some exist for purposes unique to the install grid. Each of the squares are attackable by enemy units. If you surround yourself with installed programs, they will first have to go through them before they can get you. Of course, if they destroy a program, not only will it be deleted, but any program installed off it that cannot find a path back to the hacker will also be deleted (like cutting off you hand also cuts off your fingers). Some brainstorm ideas for type of programs:
|